Gartner’s April 2024 research on Attack Surface Management states that managing complex and dispersed attack surfaces, which include supply chain touchpoints, cloud environments, on-premises systems, and SaaS applications, is becoming increasingly difficult for organizations. The scope of potential vulnerabilities has been further expanded by the growing use of containers, IoT devices, and third-party systems; therefore, security teams must implement more thorough and flexible strategies to protect their digital assets and maintain a strong reputation.
“Software is a great combination between artistry and engineering,” as Microsoft founder Bill Gates famously said. This highlights the delicate balance that businesses must strike between innovation and secure design in the context of cybersecurity. By proactively identifying and managing the numerous interconnected components that comprise today’s IT ecosystems, Attack Surface Management exemplifies this concept. By combining technical rigor with strategic oversight, ASM enables organizations to continuously assess and reduce their exposure, thereby improving their security posture rather than responding to breaches after they occur.
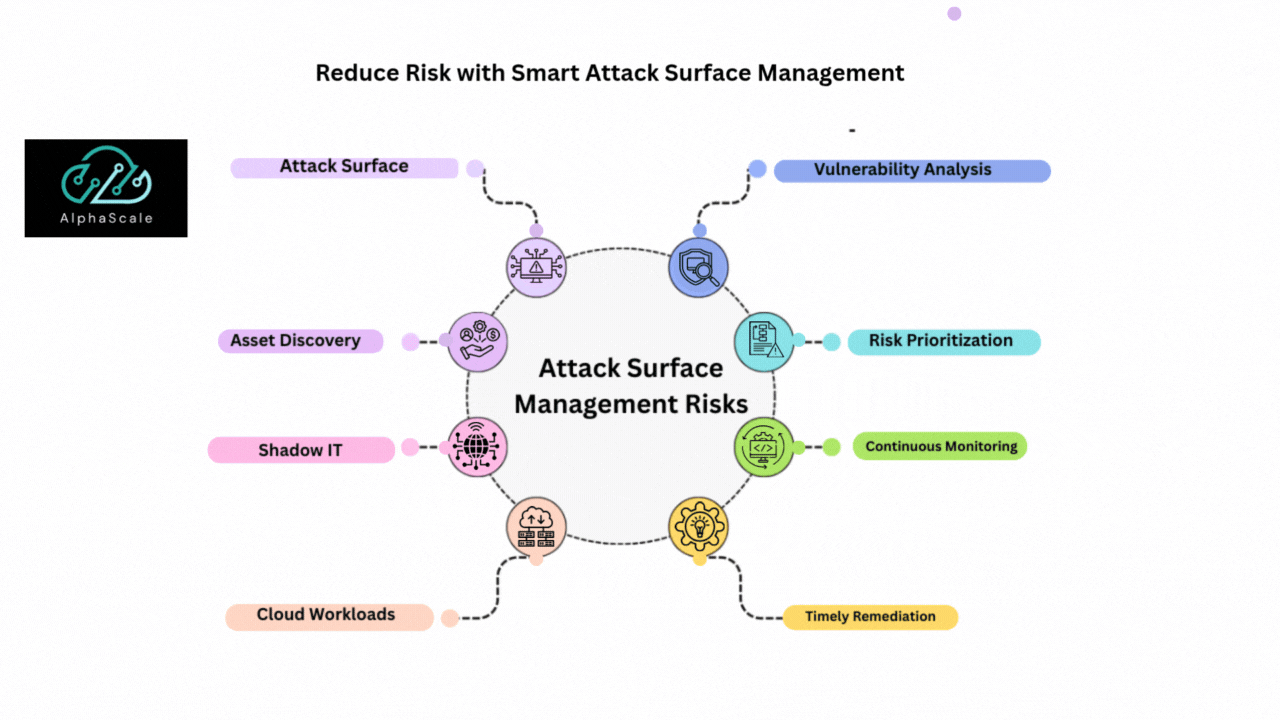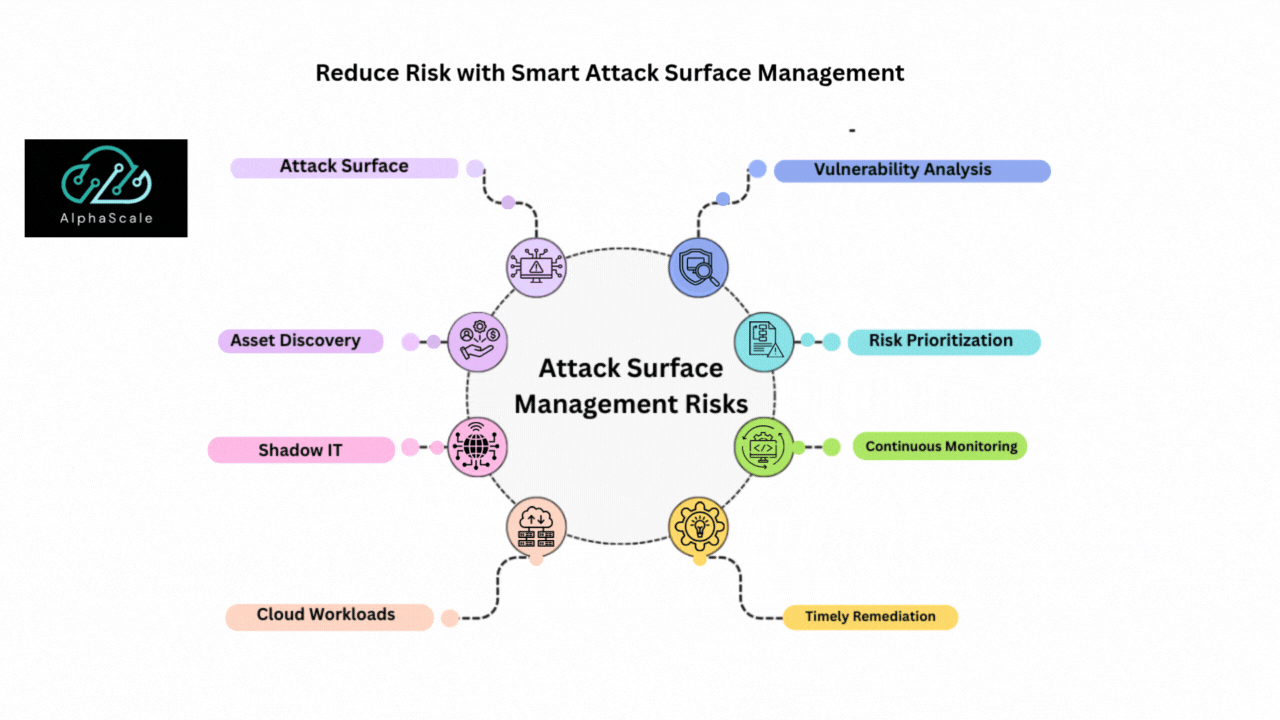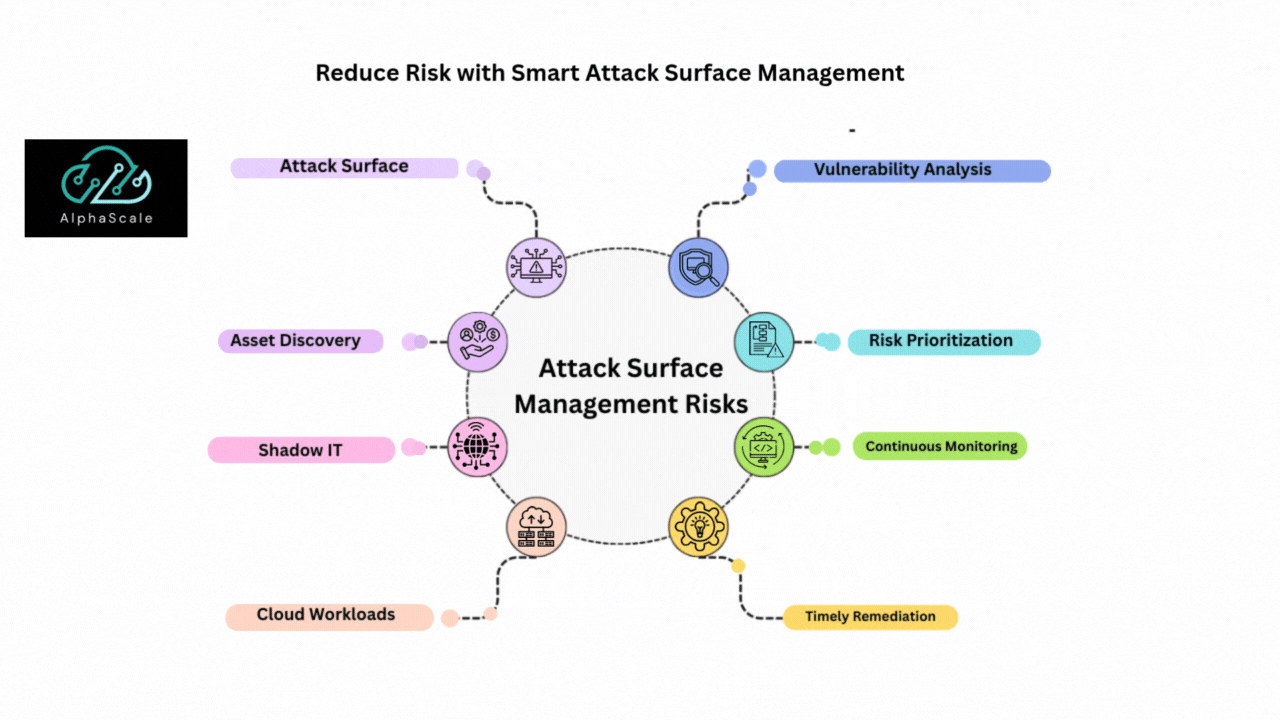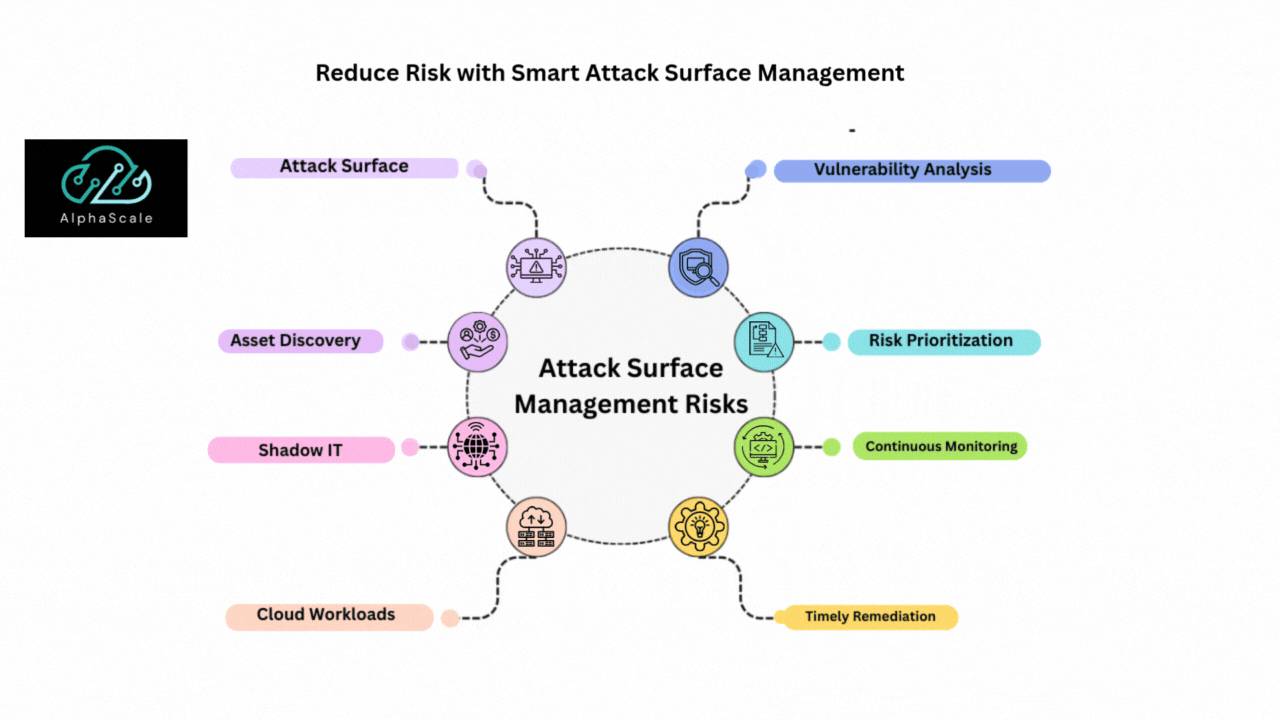
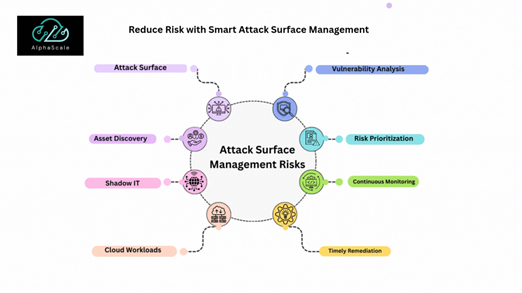
Finding All Assets to Build Strong Security
Understanding every asset linked to an organization’s network is the first step in lowering cyber risk. The crucial first step, known as asset discovery, involves locating cloud services, hardware, software, and external-facing elements, such as web applications, APIs, and domains. According to Sprocket Security, an up-to-date inventory that helps remove blind spots and shadow IT—forgotten or hidden digital assets that cybercriminals eagerly exploit—is ensured by combining continuous, automated asset discovery with manual audits.
The accuracy and scope of this inventory are increased by incorporating various data sources, including WHOIS lookups, DNS records, and certificate transparency logs. Security teams are unable to prioritize risks or evaluate vulnerabilities with confidence in the absence of this thorough, real-time visibility. Furthermore, efficient accountability and remediation planning are made possible by asset mapping that is connected to ownership and business units. With real-time monitoring and thorough risk visibility, AlphaScale’s unified security platform simplifies asset discovery.
Considering the changing digital landscape, it is anticipated that 95% of new digital workloads will be implemented on cloud-native platforms by 2025, significantly expanding the complexity and exposure of attack surfaces. To prevent exploitation, this rapid cloud adoption requires robust asset visibility and control systems.
Spotting Weaknesses and Prioritizing Risks
Determining weaknesses in an organization’s growing IT ecosystem is a constant need. To identify flaws such as unpatched software, incorrect configurations, or open ports, vulnerability analysis utilizes tools like automated scanners, penetration tests, and threat intelligence feeds. Organizations must deal with an overwhelming amount of data, underscoring the importance of risk prioritization. For instance, according to the 2023 Forrester Security Survey, 72% of security decision-makers place a high priority on systematically managing the external attack surface to lower risk exposure.
By allocating resources to high-risk areas, prioritization frameworks assess vulnerabilities based on their exploitability, potential business impact, and evolving threat trends. By implementing such frameworks, security teams can quickly and efficiently focus their patching and mitigation efforts on the most critical vulnerabilities. Real-time vulnerability prioritization is made attainable by AlphaScale’s AI-driven recommendations, which facilitate effective risk mitigation. Regular vulnerability assessments can help organizations reduce their risk exposure by as much as 40%, demonstrating the importance of timely remediation and continuous surveillance in reducing attack surface vulnerabilities.
Keep Monitoring and Work Together
As businesses implement new technologies, attack surfaces are constantly changing, necessitating ongoing monitoring. The response window is shortened by automated tools that offer real-time alerting to identify asset changes, unusual activity, or recently discovered vulnerabilities. By incorporating threat intelligence into this monitoring, situational awareness is enhanced, and new threats are identified and averted. ASM programs are further strengthened by cross-team collaboration, as connecting the business, operations, security, and IT departments ensures unified visibility and expedited remediation.
Regular employee training also enhances security awareness, which reduces the risk of human factors such as phishing and unintentional configuration errors. According to Gartner and others, executive support and group organizational effort are necessary to maintain successful ASM practices. By automating incident response through the integration of SIEM and SOAR, AlphaScale ensures prompt and well-coordinated security operations.
Using Smart Methods to Shrink Attack Surfaces
The effectiveness of ASM initiatives is increased by incorporating tried-and-true methods. By isolating systems, network segmentation restricts the movement of threats and makes it more difficult for breaches to spread. By guaranteeing that only authorized users interact with sensitive assets, strict access and privilege management reduce exposure. According to SANS Institute research, companies that implement automated patching and continuous vulnerability management lower the risk of a breach by more than 50%, demonstrating the crucial role that these integrated practices play.
The removal of redundant or orphaned assets, the strict enforcement of infrastructure-as-code to prevent insecure provisioning, the careful management of third-party risks, maintaining incident response readiness, and ensuring regulatory compliance are additional best practices. Automation is essential in all of these areas because it speeds up workflows for discovery, scanning, and remediation, which in turn reduces the attack surface and strengthens cybersecurity defenses. AlphaScale’s anomaly detection and contextual risk analysis efficiently lower false positives and increase security focus.
Building a Safer Future with Strong Security
By 2025, over 90% of organizations will embrace Attack Surface Management to keep pace with the growing complexity of digital ecosystems. Continuous asset discovery, vulnerability prioritization, and real-time monitoring are key to reducing exposure and preventing breaches. Platforms like AlphaScale empower security teams with unified, AI-driven tools that simplify management and accelerate risk mitigation across cloud, on-premises, and third-party environments.